Cyber Intelligence
We deliver the tools, techniques, and technologies used to conduct successful operations on the digital battlefield.

We deliver the tools, techniques, and technologies used to conduct successful operations on the digital battlefield.
Using advanced cyber techniques, BlueHalo’s team of technologists and analysts employ capabilities spanning traditional computing environments to Internet of Things (IoT), including offensive and defensive cyber operations and analysis, signals intelligence (SIGINT) discovery, and data science.
Full-Spectrum Cyber Operations
Effective use of technology is difficult in today's rapidly evolving technology fields, but essential for achieving mission success. Our Computer Network Operations (CNO) offensive and defensive capabilities include a focus on systems analysis, reverse engineering, tradecraft, vulnerability analysis, exploit development, and re-engineering.
Agile Development
Our engineers deliver high-value solutions from small-in-scope, high-impact applications to enterprise-wide mission applications utilizing Agile methods, while our coaches assist teams or enable large-scale enterprise Agile transformations. We work to create a cohesive rhythm across all of our engagements, both internally and with our most valued mission partners. Our dynamic leadership practices allow for the natural adoption of Agile among teams and helps build an environment for continued success.
Tactical Mission Networks
We have deep expertise in designing, developing, and implementing Tactical Mission Networks (TMNs) for critical national security agencies. We serve as the integrator, delivering the TMN with the necessary toolsets to support Digital Force Protection (DFP) and campaign requirements associated with Theater Special Operations Command (TSOC) supporting functions to Combatant Commands (COCOMs). We sustain the architecture
Digital Force Protection
Our mobility experts provide government agencies with the ability to blend Geospatial Intelligence (GEOINT) tools with Communications Intelligence (COMINT) solutions for mobile networks. Our over-the-air passive and active capabilities allow us to find the location of selectors, obtain a fix on the target, exploit devices, and analyze data and associated metadata.
Digital Operations
We possess invaluable expertise across the intelligence spectrum and can provide tradecraft expertise ranging from consultative and training services to intelligence and operations support to critical missions worldwide. We can manage identities in today's complex digital ecosystems by providing identity management solutions, ensuring users maintain access to the right systems and applications in an era of rapid technological change.
Threat Intelligence
As global and domestic threats continue to evolve, we provide actionable intelligence to customers tasked with preventing and deterring terrorism and extremism. Aligning human intelligence (HUMINT) with open-source intelligence (OSINT) and reporting, our experienced team is uniquely positioned to produce mission-critical alerts and intelligence reports.
EDEN
EDEN is a unique end-to-end data exchange solution that addresses the entire Data Lifecycle problems encountered by the USG. Our solution starts with an approved secure procurement and transport solution to move data into the exchange. An easy to use and navigate GUI will allow users to see the validated data. Viewing the aggregated data types and sources is accomplished in either an analytical or map-based view.
Learn how our Cyber experts operate at the mission’s edge.
Request Info
We maintain expertise in hardware and software reverse engineering, cyber technology development, quick reaction capability (QRC), and collection and exploitation of intelligence.
We quickly convert customer requirements into real hardware, software, firmware, and mechanical solutions in weeks, not years. With an organizational structure and design processes tailored to quick reaction, our process identifies risks that would prevent delivery and implements mitigation strategies to meet goals at mission speed.
Target Analysis & Reporting
We perform and thrive in supporting a variety of different SIGINT mission aspects, supporting sensor design, engineering, and operation on high-priority operational programs. We work in lock-step with partners to ensure the top-level performance of sensors, providing thorough analysis of sensor data, conducting intelligence analysis, and signals development and analysis, which guarantees smooth mission operations. We proffer mission accountability and sensor value analysis via multi-faceted systems engineers and data scientists by revealing unique insights into these sensors and their operations through metric capture and production.
TechSIGINT and Signals Processing
We conduct research and design, test, and deploy algorithms to process signals across software and hardware-defined systems. Using techniques like filtering, tuning, and demodulating signals, as well as additional post-demod processing, we can provide crucial support for your mission-critical systems. Whether tracking a selector, analyzing a tower or gateway, or providing finished analysis, our experience may be leveraged to provide insight not otherwise made available.
Mission Management & Signals Analysis
We support high-priority sensor operations ensuring mission assets remain optimized and potential outage threats are mitigated. Our expertise includes system and subsystem level tasking, configuration, survey, signals analysis, and maintaining system health within parameters. We ensure that selection, collection, and dataflow meet signature criteria and response. We also identify changes and anomalies within the mission environment, and process results for the normalization of follow-on analytics.
Data Science and Exploitation
As the amount of data in the world increases exponentially, gaining insights into actionable data has never been more challenging. Our data science solutions uncover information such as hidden patterns and unknown correlations to deliver mission-enabling results, enhance intrusion identification and analysis, and support signals development.
Specialized Hardware and Services
We develop and produce custom hardware and software solutions such as embedded systems, analog and power systems, data interfaces, RF systems, full board design, and mobile and web services to support our customers’ cyber initiatives.
Researching and Prototyping
Our applied research and prototyping capabilities enhance or automate analytic capabilities, increase knowledge of adversarial threats, and enable new CNO capabilities.
Learn how our analysts can provide actionable intelligence.
Request Info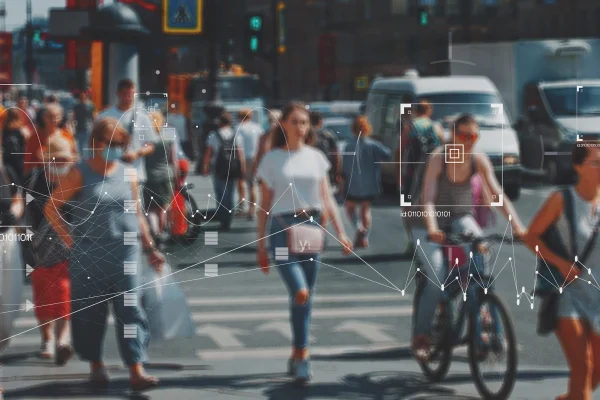
Open-source Intelligence
BlueHalo’s open-source intelligence (OSINT) engineers and Deep Web experts combat emerging multi-domain and near-peer global threats by collecting and analyzing electronic signals and open-source intelligence to determine adversarial capabilities, intent, and actions before they happen. We perform all-source investigations, including social media analysis, making connections from the dark web into the open web, and creating targeting profiles for organizations and individuals.
Scraawl
BlueHalo’s AI powered Scraawl OSINT Analysis product leverages the largest data store in the word, PAI, to provide unique insights and solve DoD and commercial challenges. Use cases for our image and video analytics tools include face detection and recognition, target identification, and tracking. Our text analytics leverage natural language processing (NLP), graph analytics, behavior analytics, and trend analysis to help users obtain actionable intelligence from large datasets.
Sensor Performance
The Sensor Effectiveness Tool (SET) incorporates subject matter expertise to scientifically evaluate a sensor’s capability, assessing how well radar systems can support intelligence objectives against select targets and geometries. Underlying technology can be expanded to other sensor systems.
National Intelligence Analysis
Our team helps decision makers understand the value of intelligence to guide technology investment decisions. We provide lifecycle operational support for critical initiatives (Joint Land and Component Constructive Training Capability, Entity Resolution Federation (JLCCTC ERF), Battle Command Training Facilities, National Air & Space Intelligence Center (NASIC)).
Join the BlueHalo team to experience the satisfaction of providing highly innovative solutions to complex technical problems–and doing it with a team that feels like family, supported by a company committed to developing and caring for our people and providing industry-leading compensation and benefits.
We’re looking for team members:
Front-End Devs
Build elegant and powerful tools and applications across a variety of modern web frameworks and technologies. If you share our passion for user experience and accessible design, come talk to us!
DevOps
Design and manage secure, scalable, cloud-based tools and applications using modern orchestration technologies. If your goal in life is to automate and containerize everything, you’ll fit right in.
Full-Stack Devs
Build and deliver end-to-end solutions to important problems using modern programming languages and frameworks. When encountered by any daily inefficiency, if your first thought is “I could write a program for this!” this is the place for you.
Cloud Engineers
Design, build, and deploy efficient multi-cloud enterprise solutions in a lively yet laid-back environment full of people who love learning and solving hard problems.
View Our Open Positions and Transform Your Career.
Join Our Team